"The aim of the intrusion detection program (or IDS) is to identify unauthorized accessibility or mistreatment of your computer system system. Invasion diagnosis methods tend to be a lot like robbery wireless house alarms pertaining to pcs. They appear sensors and occasionally carry corrective motion when the burglar as well as abuser can be diagnosed. A variety of attack prognosis methods happen to be created though the diagnosis plans generally fall under 1 of 2 groups, anomaly discovery as well as mistreatment recognition. Anomaly sensors look for behaviour which deviates through regular system use. Wrong use alarms try to find behaviour of which fits any regarded episode circumstances. Significant amounts of commitment continues to be dedicated to breach recognition, which record offers back links to many people internet sites that examine many of these efforts"(http: //www. cerias. purdue. edu/about/history/coast_resources/intrusion_detection/)
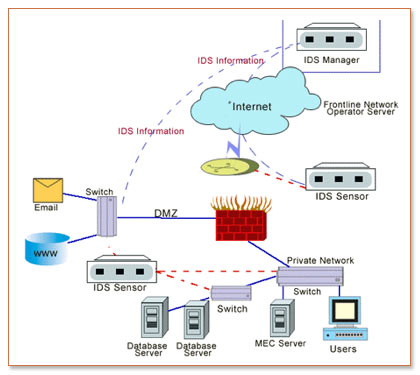
You will find there's sub-category involving invasion detection devices named system intrusion detection programs (NIDS). These methods watches packets within the circle wire in addition to seeks dubious exercise. Network invasion recognition programs can certainly keep an eye on a lot of pcs at any given time spanning a multilevel, whilst various other attack recognition devices may perhaps keep an eye on only one. Tips to Hack WiFi Password.
Who's going to be breaking in the body?
Protection afford, one particular common belief regarding application cyber criminals can be it's normally men and women outside the house ones community that split in your own methods and also bring about chaos. The truth, specifically for company employees, can be in which insiders can and typically carry out result in a lot of safety breaches. Insiders typically impersonate people with far more protection under the law after that on their own to gain access to hypersensitive data.
How can burglars break in your system?
Most effective in addition to easiest way for you to separate with would be to enable a person get bodily use of something. Despite the best of efforts, choosing unattainable to stop an individual after they get actual physical usage of some sort of equipment. Also, in the event somebody has a consideration using a technique previously, in a reduced agreement level, another strategy to separate inside is to use tricks on the trade to be granted higher-level legal rights as a result of slots within your process. Ultimately, there are many solutions to gain access to techniques regardless of whether is doing work remotely. Out of the way attack tactics are getting to be more challenging and much more sophisticated in order to combat.
So how exactly does one stop intrusions?
There are numerous Freeware/shareware Intrusion Discovery Systems along with business breach recognition devices.
Open up Supply Attack Prognosis Programs
Listed below are with the available origin attack diagnosis devices:
ASSIST (http: //sourceforge. net/projects/aide) Self-described since "AIDE (Advanced Invasion Recognition Environment) is a totally free alternative to Tripwire. And also a similar issues since the semi-free Tripwire plus more. You'll find other no cost substitutions obtainable why then make a completely new a single? All the other substitutions tend not to achieve the quality of Tripwire. As well as I desired a course that would meet or exceed this constraints connected with Tripwire. "
File Method Saint (http: //sourceforge. net/projects/fss) - Self-described seeing that, "File Technique St is usually a light host-based attack recognition technique with primary concentrate on velocity and usability. inch
Snort (www. snort. org) Self-described since "Snort is usually an open up supplier circle attack deterrence along with recognition system employing a rule-driven vocabulary, which in turn includes the main advantages of signature bank, method and anomaly based check up techniques. Using countless downloads as of yet, Snort would be the nearly all widely started intrusion recognition and also reduction technological innovation around the world and also is just about the de facto normal for the sector. inch
Tidak ada komentar:
Posting Komentar